Kongtuke Powershell Malware Notes (01/06/2025)
Basic Static Analysis
Source: Malware Bazaar
WARNING: these are live malware zips that may cause harm to your PC and network, so download them at your risk
Stage 0
- Notes:
- File is a standard powershell script with most of the obfuscation being simple chains of algorithmic equations converted to command values
Stage 1
Notes:
Zip - password: infected
Took a bit of work, but I was able to get the initial script readable
The vast majority of this particular stage involved the following:
running each algorithmic chain through Powershell to get their final value (with most of the obfuscation turned off)
the most notable two techniques used involved passing instructions through $null and then obsfucating with a string (for first one) and then using that output to xor decrypt a GZip compressed stage 2 payload
the fourth, fifth and six steps (labeled
$settings_new, $setting_old, and $settings_overridein the zip file) all passed a chain of instructions involving mostly reading and writing to disc with$settings_overridebeing ammended to the bottom of$settings_old, making it possibly a form of obfuscation
Stage 2
Notes:
Zip - password: infected
After demangling the payload from the previous stage, the purpose of this payload was as follows
checked if PC was a virtual machine (which it immediately figured out due to two strings passing VMWare information directly to the bot)
instead of killing itself upon observation discovery, it added seemingly random values to what I called the $VM_probability variable; when reaching out to the botnet at the end of the chain, this information would get passed with the URL, most likely to notify that my system was one to watch and / or to send a dofferent payload back
Basic Dynamic Analysis
Notes:
Detonating it had some garbage on both PowerShell 5 and 7
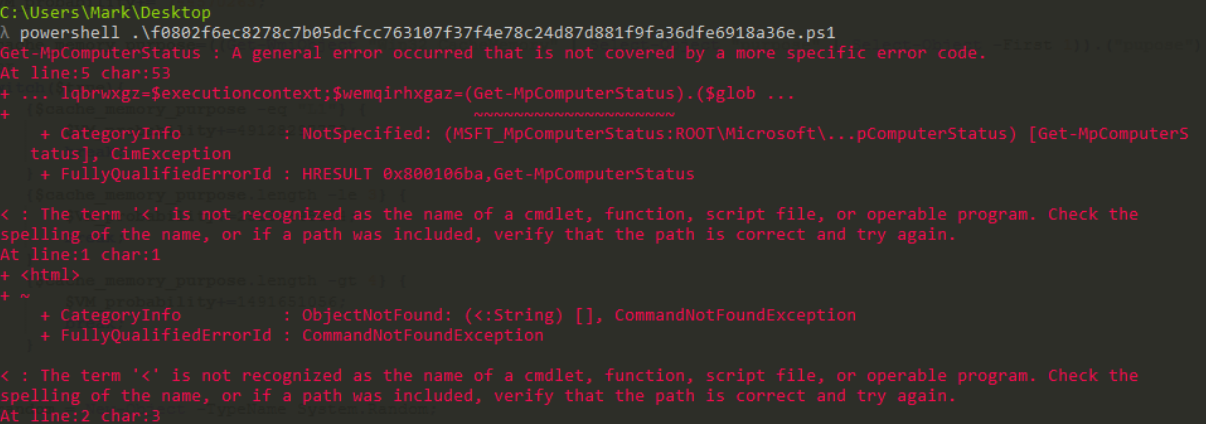 due to Get-MpComputerStatus (a check for wheter or not an antivirus could be found - source) failing (but still grabbing what was probably the required information)
due to Get-MpComputerStatus (a check for wheter or not an antivirus could be found - source) failing (but still grabbing what was probably the required information)There was an HTML file being read and called upon that I didn’t find in my initial tests; I’m guessing there was an extra payload I missed by demangling everything or it could have been a result of curl being used without a network connection
Manually setting the stage 2 payload to pass the VM check got me as far as a brief popup on only Powershell 7 about needing to sign in as a user named “seb”
- Who is this seb? Is this a signature or possibly just a quirk of my Malware Analysis setip? Haven’t found much about this individual yet and it only appeared in Powershell 7
MalwareBazaar classified this as a KongTuke (see the link up top), and after looking at other samples from the same batch, I can see why
the IOC is the obfuscation; all KongTuke samples I’ve looked at use a similar structure to what was posted above